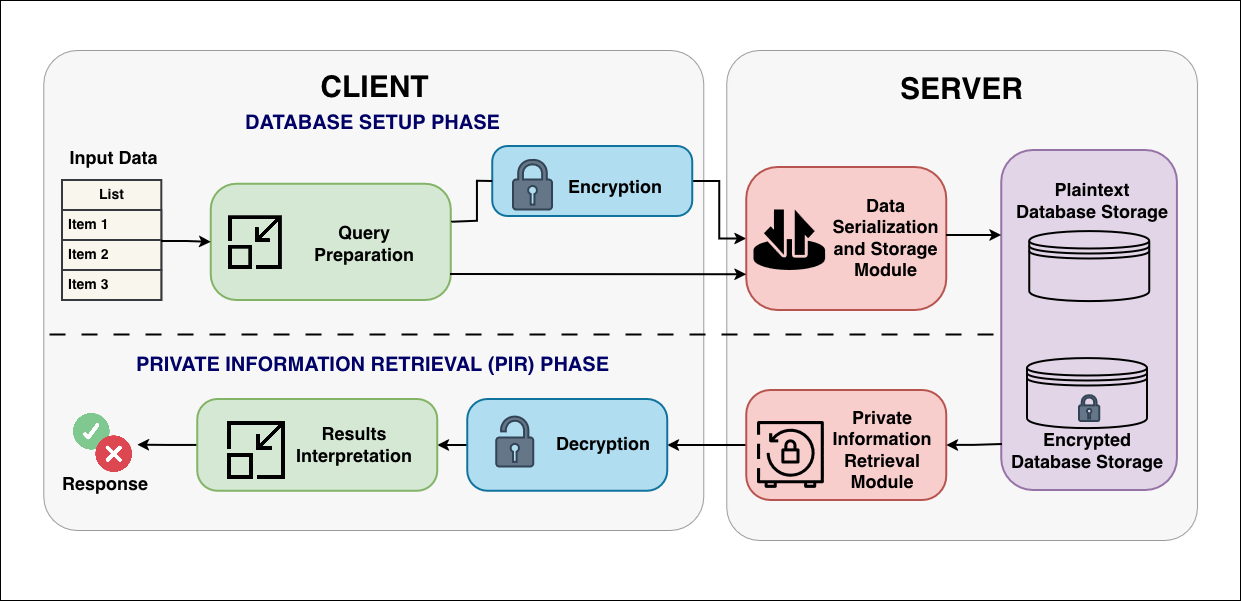
Outsourced Private Information Retrieval System
Private Information Retrieval (PIR) is a fundamental cryptographic building block that plays a crucial role in preserving data privacy in modern information systems such as anonymous communication and private safe browsing. The primary goal of PIR is to enable a client to query and retrieve specific information from a remote database without revealing to the server which item was accessed. In other words, while the client successfully obtains the desired information, the server remains oblivious to the nature of the query. This property is essential in scenarios where access patterns alone can leak sensitive information, such as in healthcare records, financial transactions, or search histories. In this post era of quantum computing, the problem of PIR also persist leading to this work that focus not only on building secure PIR systems but quantum-resilient PIR.
The technical contributions of this work are:
- We propose a Homomorphic Encryption based Private Information Retrieval that enables users to retrieve complete database records without revealing to the server which specific index or entry was accessed in the database. This protocol supports efficient, non-interactive queries suitable for real-world deployment scenarios.
- We introduce a database and query encoding scheme that leverages the polynomial structure of state-of-the-art Homomorphic Encryption schemes to compactly represent all attributes and records in a database. This design enables parallel computation across records and improves efficiency for real-world retrieval scenarios.
Background
Homomorphic Encryption based private information retrieval offers one of the most efficient approaches to achieving query privacy, combining minimal communication overhead with reduced computational complexity. The protocols are inherently non-interactive, requiring only a single round of communication between the client and the server. This non-interactive nature significantly improves practicality, making such protocols highly attractive for deployment in large-scale systems and cloud environments. The distinguished efficiency and strong privacy guarantees of these systems not only strengthened its theoretical foundations but have also led to its adoption in real-world applications. A notable example is the recent integration of a PIR system built upon the BFV scheme by Apple to enhance email privacy.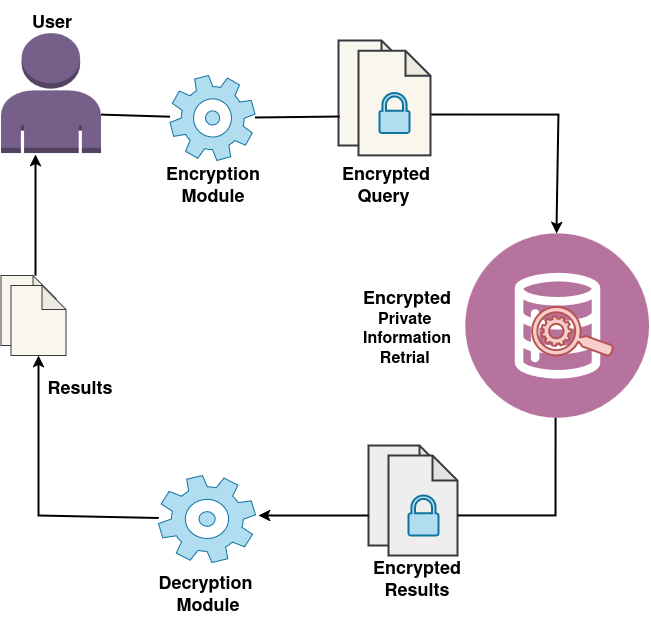
Capabilities
Our system enables fully encrypted computation, where all query operations are performed directly on encrypted data. This ensures that sensitive information remains confidential throughout the computation process. Users can execute complex operations without ever revealing plaintext values, combining strong security with efficient, practical performance suitable for large-scale deployments.
The system provides robust query and database privacy. The server executing retrieval operations cannot determine which index is being accessed, safeguarding user queries. Additionally, intermediate results never expose plaintext database information. By performing identical computations for every query, the system prevents access-pattern leakage, ensuring that no information can be inferred from the server's behavior.
Our system is also flexible and interoperable with existing homomrophic encryption pipelines and supports both ciphertext and plaintext databases. Retrieval outputs can be fed seamlessly into downstream encrypted computations, enabling complex, multi-step privacy-preserving workflows.