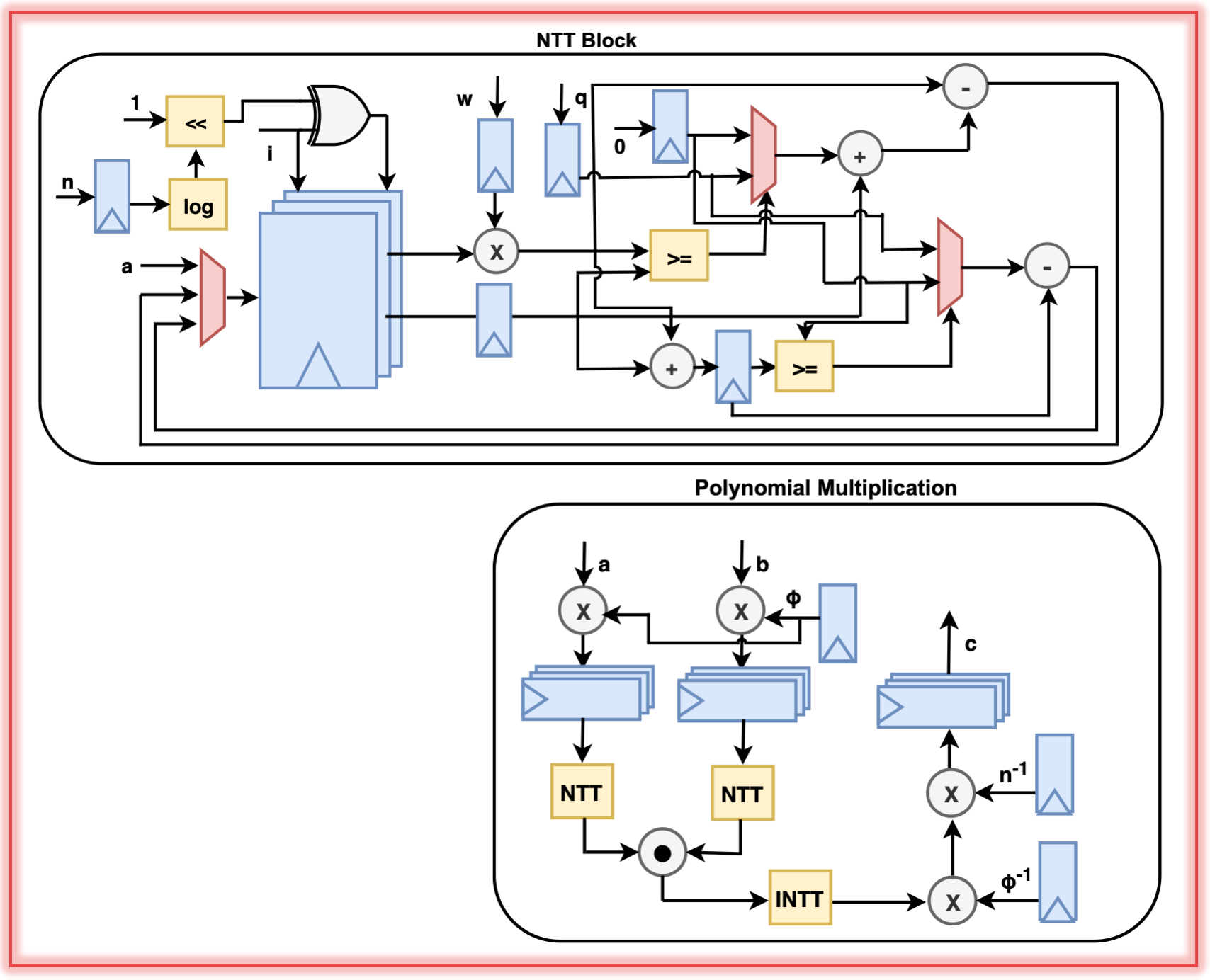
The entire team of PQC Secure is very excited to introduce
FHEON.
FHEON is an open-source, privacy-preserving neural network framework designed to simplify the development of encrypted machine learning models.
Built on the CKKS homomorphic encryption scheme and OpenFHE, FHEON provides a suite of highly efficient, robust, and fully configurable neural network layers such as;
convolution, average pooling, fully connected, and activation layers.
Each layer accepts a set of parameters familiar from traditional machine learning frameworks, such as input/output channels, kernel size, stride, and padding.
This makes it easy to design arbitrary CNN models in the encrypted domain while maintaining a workflow that feels intuitive and conventional.
Beyond its layer implementations, FHEON includes a set of utility functions that streamline integration, reduce complexity, and accelerate adoption.
Together, these components enable researchers and developers to build encrypted neural networks without compromising flexibility, usability, or efficiency.
Visit the FHEON documentation, featuring a comprehensive suite of examples, at
FHEON Website,
and access the code repository at
FHEON on Github.
We are excited to hear your feedback and ideas as we continue to improve the framework.