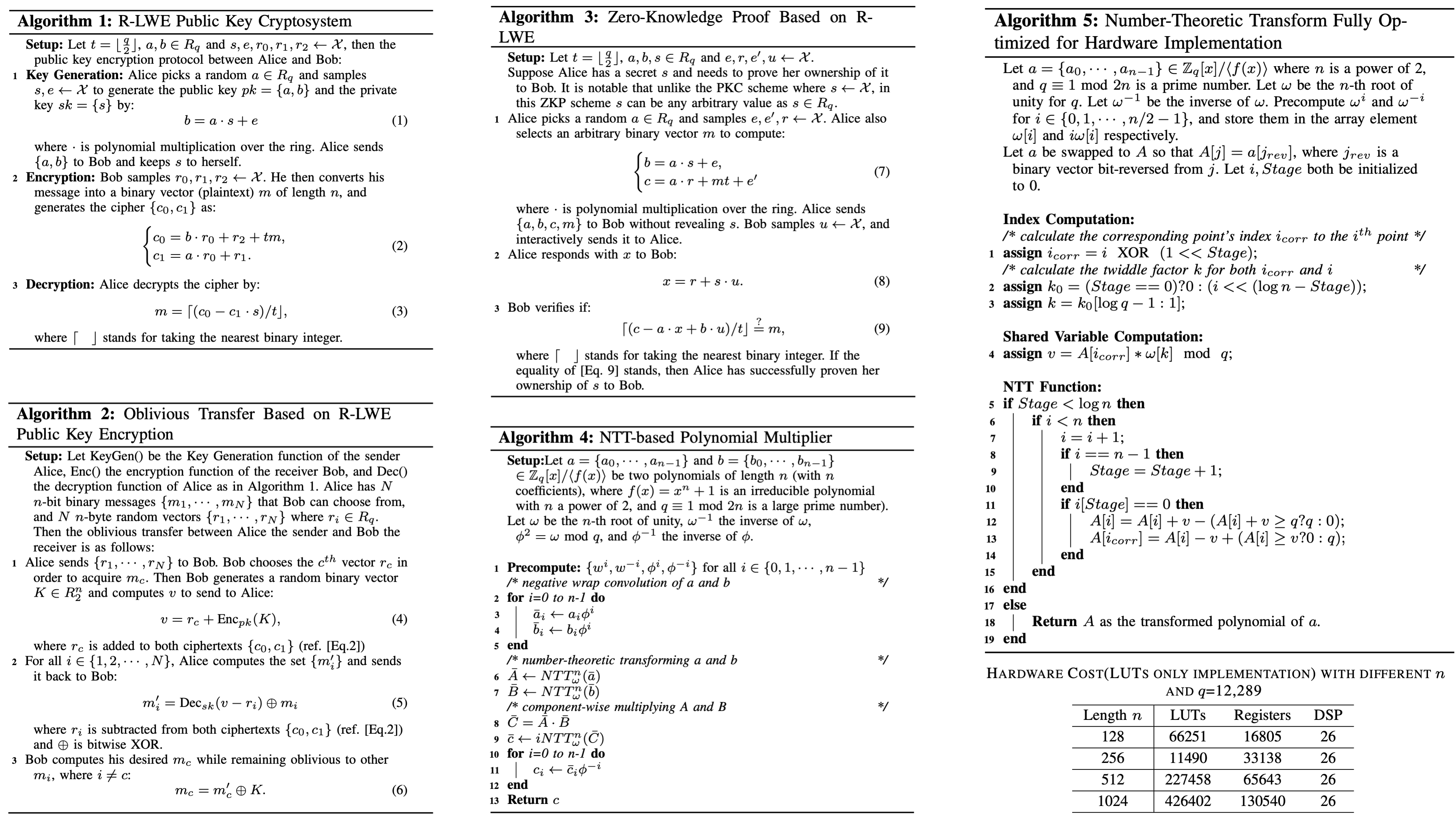
Hardware Post-Quantum Cryptographic Library
As quantum computing becomes increasingly viable, the need for quantum-resistant cryptographic systems has become critical in secure computing design. In response, our research & Development team has developed a comprehensive hardware library of post-quantum cryptographic primitives (PQCPs), encompassing four essential components:
- Public Key Cryptosystem (PKC)
- Key Exchange (KEX)
- Oblivious Transfer (OT)
- Zero-Knowledge Proof (ZKP)
The technical contributions of this work are:
- FPGA-optimized implementations of PQCPs, including novel algorithmic designs for OT and ZKP.
- Algorithmic enhancements that minimize area and latency overheads while maintaining robust security guarantees.
- Open-source, synthesizable, and verifiable RTL code for community adoption.
The RTL framework is fully parameterizable and includes a high-efficiency, N-point Number-Theoretic Transform (NTT) module for accelerated polynomial multiplication—essential for lattice-based cryptosystems.
Background
Recent advancements in quantum computing have made it increasingly clear that functional and widely accessible quantum systems are on the horizon. These machines promise a dramatic leap in computational capabilities, enabling efficient solutions to problems that are currently intractable, particularly those classified as NP-hard on classical architectures. While this progress opens new avenues for innovation, it also poses a significant threat to existing cybersecurity frameworks. Many classical cryptographic schemes, such as RSA, ECC, and ElGamal, rely on mathematical problems like integer factorization and discrete logarithms, problems that quantum algorithms can solve efficiently. As a result, these systems may soon become obsolete or severely compromised. In response, the cryptographic community has initiated a global effort to develop and standardize a new generation of post-quantum algorithms designed to withstand quantum-enabled attacks.In early 2017, the National Institute of Standards and Technology (NIST) initiated a formal process to standardize post-quantum cryptographic algorithms. The first round saw 69 candidate submissions, with 27 advancing to the second round. Among these, the Ring-Learning with Errors (Ring-LWE) approach emerged as the most widely adopted, appearing in 12 of the 27 second-round candidates.
Ring-LWE-based cryptosystems offer several compelling advantages:
- Lattice-based security reductions—such as modified shortest vector problems—remain computationally hard even for quantum computers.
- Compact key sizes compared to other schemes with similar security guarantees.
- Support for homomorphic encryption, enabling secure computation on encrypted data.
- Hardware efficiency, making Ring-LWE well-suited for high-performance and resource-constrained environments.
Capabilities
The team has capitalized on the strengths of Ring-LWE to develop efficient hardware implementations tailored for post-quantum cryptography. While numerous software-based explorations of Ring-LWE exist, hardware-level design space exploration remains relatively underdeveloped. Among the few existing hardware implementations, scalability and performance optimization are often overlooked. A key technical challenge lies in executing large-scale polynomial operations over finite rings, core computational tasks in Ring-LWE schemes, which continue to pose significant difficulties for hardware designers.To address the challenges of scalable and efficient post-quantum cryptographic design, we have developed a suite of highly optimized, parameterizable hardware modules that serve as foundational building blocks for accelerated design space exploration, particularly for systems based on Ring-LWE algorithms. This hardware primitive set includes four widely used cryptographic components:
- Public Key Cryptosystem (PKC)
- Key Exchange (KEX)
- Oblivious Transfer (OT)
- Zero-Knowledge Proof (ZKP)
PKC and KEX form the backbone of modern secure communication protocols. OT is essential for privacy-preserving applications such as secure genomic data queries and private machine learning. ZKP, meanwhile, is increasingly recognized as a key enabler for next-generation blockchain technologies and other trustless systems.